It is nowadays simply too easy to manipulate network traffic. There is for example a Chinese Software called Netsense, which makes it so easy, smooth and effortless, the people using it really might not even know it's using illegal techniques. I don't have any idea, though because I don't know what the manual or description says -> I don't speak Chinese.
ARP is the address resolution protocol. It resolves a computer's IP address to a computer's hardware MAC address. ARP poisoning means that one computer(A) claims to be the owner of the IP address of another computer(B). Computer(A) then gets all network traffic destined for that computer(B). This would mean that the computer(B) the network traffic is actually destined to would not get it anymore. Therefore the spying host(A) is usually configured to forward the packages to the actual host(B) after inspecting them.
Now let's see what you can do against ARP Poisoning under Linux.First let's find out, what's going on. For that purpose wireshark is very helpful. Wireshark displays all network traffic on your interface. For our purposes we do not need to use the promiscuos mode, as we only have to see the packages directed at our machine. If you want to watch for other machines being poisoned you need to activate the promiscous mode. Usually activating it shouldn't hurt, so let's activate it.
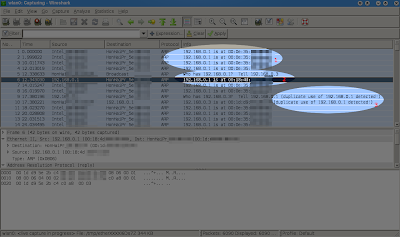
What you will see characteristically is that (1) one hosts keeps announcing its MAC address via ARP without any other hosts actually having asked for it beforehands. Wireshark may detect a duplicate use of IP addresses (3). And the normal ARP resolutions process(2) of a host asking for the IP address and then gettings its answer usually does not happen anymore for that particular address. (1) is called IP spoofing, as a host claims to have an IP address which it actually does not.
Let's see what we can do about it. There are two things you can do. The easy one, which works under Windows as well, is to set the MAC address manually, called static mac assignment. Type in run, or in a console:
arp -s 192.168.0.1 00-12-34-56-78-90You should replace 192.168.0.1 with the ip address of the host that is constantly shown in (1) and the mac address behind it with the real mac address of that host, which you can either look up manually or if you're lucky, see as in (2), e.g. when the ARP poisoning is not active at the moment.
Under Linux you can often chose a more flexible approach and simply ban the host that is poisoning your machine. Now don't even try using the normal iptables against it, in my tests it had absolutely no effect. But there is a version of it called arptables, which can help you.
sudo arptables -A INPUT -m mac --source-mac ff:ee:dd:cc:bb:aa -j DROPWhile ff:ee:dd:cc:bb:aa should be replaced with the mac address of the host that can bee seen as sources mac address in (1). Now the host should not be able to poison your arp table (or communicate with you) anymore at all. Of course you can also just manually set the IP address just as under windows above
sudo arp -s 192.168.0.1 00-12-34-56-78-90This will still allow the host to communiate with you.
To check what hosts and what mac address are in the arp table simply use
sudo arp
Remember that while the ARP poisoning is active and working, the hosts poisoning your arp table can usually see all your network traffic. This means the host can log and save everything in your network traffic, such as your passwords, emails, instant messages and everything that is not or poorly unencrypted, even some poorly configured online banking pages. It will most probably also have an impact on the connection speed, especially if you're using a wireless network with a bad reception.
I hope it helped. Any questions or remarks in the comments are welcome.
No comments:
Post a Comment
I appreciate comments. Feel free to write anything you wish. Selected comments and questions will be published.